
This guide explores the key insights and strategies we used and the lessons we learned from moving into our new premises.
Download
Small-to-medium businesses can remain agile by embracing technology to fuel their long-term strategy and lessen the impact of inflation.
Download
The role of the CIO has evolved over time. This eBook examines an emerging alternative worth considering, the Virtual CIO (vCIO).
Download25/11/2025
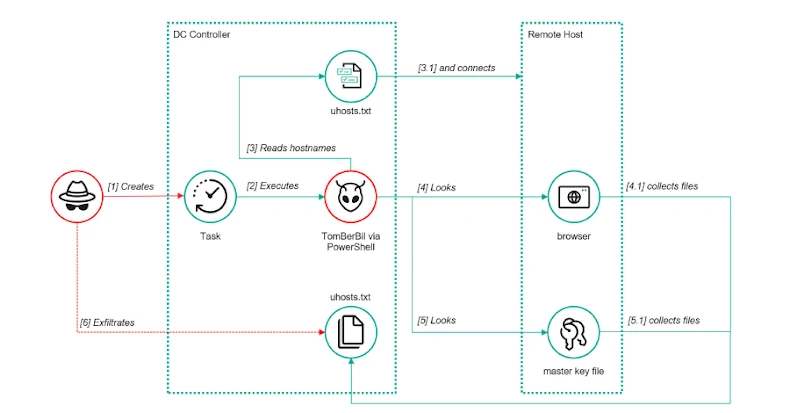
The threat actor known as ToddyCat has been observed adopting new methods to obtain access to corporate email data belonging to target companies, including using a custom tool dubbed TCSectorCopy. "This attack allows them to obtain tokens for the OAuth 2.0 authorization protocol using the user's browser, which can be used outside the perimeter of the compromised infrastructure to access corporate mail," Kaspersky said in a technical breakdown.
Read More19/11/2025
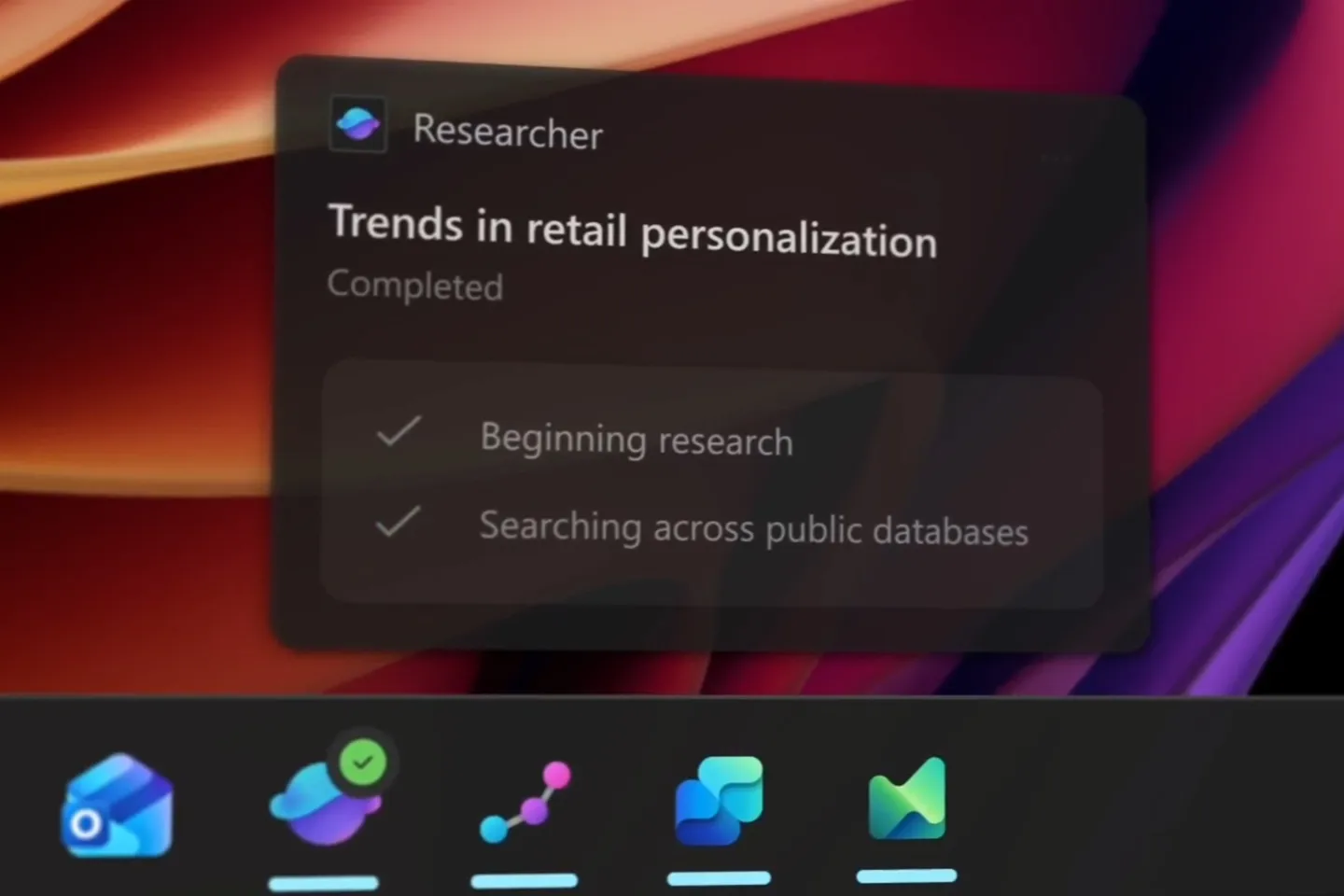
Microsoft is trying to transform Windows into a “canvas for AI,” with new AI agents integrated into the Windows 11 taskbar. These new taskbar capabilities are designed to make AI agents feel like an assistant in Windows that can go off and control your PC and do tasks for you at the click of a button. It’s part of a broader overhaul of Windows to turn the operating system into an “agentic OS.”
Read More18/11/2025

The rise of the Tycoon 2FA phishing kit should serve as a global warning siren for every enterprise. This is not a tool for elite hackers. This is a turnkey kit that anyone with a browser can use to bypass the very MFA and auth apps companies depend on. And it is being used at scale. Over 64,000 attacks have already been tracked this year, many targeting Microsoft 365 and Gmail because those platforms represent the easiest, fastest path into an enterprise.
Read More30/10/2025

There has been a tremendous amount of conversation lately about artificial intelligence and what it means for cybersecurity. Depending on who you talk to, AI is either going to replace every job in the security industry or it is going to fade into the background as just another tool in an already overloaded technology stack. The truth, as usual, lives somewhere in between those extremes.
Read More24/10/2025

Microsoft is currently working on a new Teams feature that will use Wi-Fi network connections to pinpoint a user's exact location. For context, Teams will automatically update a user's work location when they connect their device to an office Wi-Fi network.
Read More17/10/2025
.webp)
Anthropic is integrating its Claude AI assistant with Microsoft 365 services so it can surface content from Word documents, Teams messages, and Outlook emails in conversations with the chatbot. It’s part of a series of updates to Claude to make the chatbot more useful at work.
Read More30/9/2025
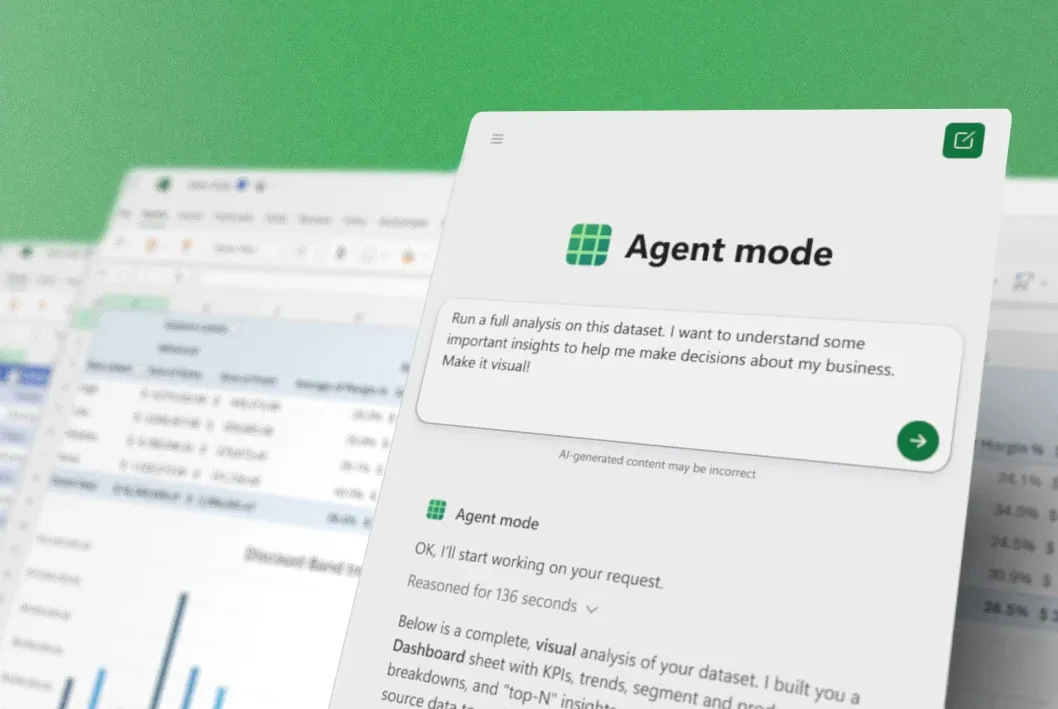
The software maker is launching a new Agent Mode in Excel and Word that can generate complex spreadsheets and documents with just a prompt. A new Office Agent in Copilot chat, powered by Anthropic models, is also launching today that can create PowerPoint presentations and Word documents from a “vibe working” chatbot.
Read More23/9/2025
A sophisticated malware campaign has emerged that leverages fake online speed test applications to deploy obfuscated JavaScript payloads on Windows systems. These malicious utilities masquerade as legitimate network speed testing tools, manual readers, PDF utilities, and various search frontends to deceive unsuspecting users into installing dangerous code that operates covertly in the background.
Read More22/9/2025

Attackers are increasingly sending phishing links over non-email delivery channels like social media, instant messaging apps, and malicious search engine ads. This article explores why phishing attacks are moving away from exclusively email-based delivery, and what this means for security teams.
Read More